VertexNet Loader crimeware timeline, popular functions and marketing schene
This is a known crimeware package whose the first version was released in March 2011 and which is used to create automated malware with antivirus evasion functions, allowing managing data, and also stolen through malware created by a web application. That is, designed to create HTTP-Based Botnets.
While crimeware is a general purpose, the highest percentage of malicious focus is based on the arbitrary collection of sensitive data from each of the computers infected by a keylogger component. Your name (VertexNet) corresponds to the fusion of the words Vertex, referring to the concept that describes the point in geometry where two or more rays that form an angle; and NET, referring to the creation of computer networks.
Timeline
Functions
The information obtained from each infected computer is stored in the database automated crimeware then be visualized in a simple and readable through the panel of statistics. These data are comprised of the following parameters:
uid: Unic user identifier = HWID + first drive
serial.
lan: IP adress local area network.
cmpname: Computer name.
country: Computer country.
idle: Last user activity in seconds.
cc: Country Code #FR, #US, #DE, etc.
ver: Loader version.
VertexNet basically consists of four modules. Each is responsible for specific tasks ranging from opening a remote shell (backdoor) to record activities on infected systems (keylogger). The modules are:
Modules list.
Keylogger logs.
Read file.
Remote shell.
VertexNet has a series of commands that run automatically with each report that is made from the infected computer to the C&C, each update the bot and depending on the settings from the control panel designed for the future attack and infection process . The commands list is as follows:
msg:: = This function send a sample messagebox
to the target computers.
exec:: = Equivalent to the "execute"
dialogue of Windows.
close = Close the loader of selected computers.
urldl:: = Download and execute a binary file in
selected computers.
getproc = Process list from selected computers.
getmodules:: = List process ID.
setkeylogger:: = Active or unactive the keylogger
module.
getklogs = Retrieve the logs from selected
machines.
readfile:: = Retrieve the content of a file in
text format.
uninstall = Close the loader and uninstall the
startup key.
httpflood:: = DDoS attack.
remoteshell:: = Execute a shell.
visitpage:: = Simulate a website visit during
few seconds.
Marketing no-improvised and mismanaged egocentrism
In the "footer" of the main panel of VertexNet you can read the following legend related to the development of crimeware:
VertexNet - Loader coded by DarkCoderSc
(PHP/C++)
DarkCoderSc Software © since 2006
unremote.org
DarkCoderSc Software © since 2006
unremote.org
Of course DarkCoderSc is the "under" nickname by which the developer makes known crimeware, but the year 2006 (as noted above) not the creation of VertexNet year but the year from which this person came to develop applications to facilitate the creation of malware, theft of sensitive information, antivirus evasion and unauthorized remote control of infected computers. While the original website is out of operation, there are other commonly used mirrors to download VertexNet Loader.
In recent years, crimeware developers have expanded the advertising will start to use public channels and social networks to spread crimeware created. Concrete examples have also been the first to use this methodology, so far not so common in the cybercrime environment were Unique Sploits Pack and YES Exploit System.
In this sense VertexNet is no exception and in fact the author seems to possess a high level of self-centeredness and well made. VertexNet has its own website which is basically the same template used for the crimeware.
The VertexNet marketing campaigns are carried out through various social networks all under the same "under" nickname, including: Google+, Facebook, Twitter and a YouTube.
But ... Who is DarkCoderSc? Besides being the developer of another utility designed as malware: DarkCometRAT. A RAT (Remote Administrator Tool) that has several features such as control equipment, including Linux and MacOS running a Windows emulator like Wine, violating the privacy of victims taking screenshots of the desktop, enabling the webcam or run DDoS attacks, among others.
Since February 2012 it's also admin in OpenSC, a popular cybercrime community and according to public information extracted from one of its websites, the real DarkcoderSc name's would "Jean-Pierre LESUEUR, i’m born in 1990 London and living since 1993 in
Paris suburb" with the next contact information: Skype ID: DarkCoderSc / email: darkcodersc@gmail.com
/ Phone: +336 52805884 and +339 72320273.
Will real data? This is your LinkeIn profile:
And this
your CV:
Yes, the data are real. However, Jean-Pierre is a software developer and had to deal with anticipated problems and serious consequence of these developments, for which earlier this year was forced to suspend the maintenance and updating of these programs, in the words of his own: programs classified as malware.
Hopefully now use his good knowledge for the constructive development of software for the Security Community.
All data are public because maybe, unlike professional cybercriminals who hide under the protection of specific forums, it seems that Jean-Pierre had nothing to hide. The truth is that their developments are widely used in the cybercrime scene to generate DDoS attacks and steal information from users all around the world.
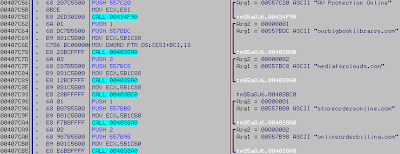
Some simple intelligence
for identification of this crimeware
/imgs/saria.png: you can see a fine image.
/imgs/vabout.png & /imgs/logo.png: you can see the VertexNet logo.
** This information changes depending on the crimeware version.
/css/style.css: you can download the VertexNet website style. This file has the next MD5
hash A889B28CE62AF463A7B7FEFFA191442D
More simple
and advanced intelligence about this crimeware in CAS - CrimewareAttack Services -, a private
service of MalwareIntelligence.
Alex.